The robust evolution of IT technologies allows businesses to build complex networks.
Inside these systems lies all their touchy data, be it private business information or installment cards information, which draws in proficient programmers and content kiddies alike.
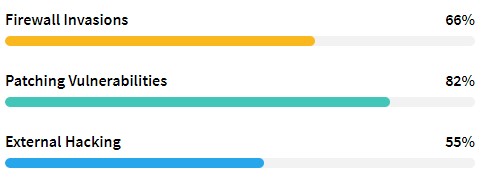
Figure: Network Attacks
While arrange level vulnerabilities may be less normal, their effect is difficult to overestimate. With access to a system, a pernicious client may get delicate information and plan financial misrepresentation or plant malware for upsetting business capacities.
Fixing your system border is of prime significance for each association, paying little respect to its size. System entrance testing serves to:
- Enumerate security vulnerabilities of system foundation, including the frameworks, administrations and system gadgets
- Become mindful of the security dangers postured by the found vulnerabilities
- Learn the manners by which arrange vulnerabilities may affect a business procedure
- Identify introduction to inward (i.e. malevolent workers) and outside assailants (i.e. unknown assailants on the Internet)
- Receive down to earth remediation proposals for the revealed issues
- Become consistent with security controls, (for example, prerequisite 11.3 of the Payment Card Industry Data Security Standard (PCI DSS))
Spiral World security engineers are specialists in organize entrance testing. The group uses our restrictive system in view of Best Practices and industry-standard structures, for example, OSSTMM, OWASP, WASC. Spiral World security pros use both computerized and manual methods, to guarantee the most abnormal amounts of system security.

