In the course of the most recent decade, static sites have developed into exceedingly useful web applications which regularly give access to touchy information and basic business capacities. Web applications get client info and pass it to back-end frameworks, which make them potential portals for an extensive variety of assaults. Without a legitimate shield, a web application could be utilized to take touchy information which may eventually prompt a harmed business notoriety and money related misrepresentation.
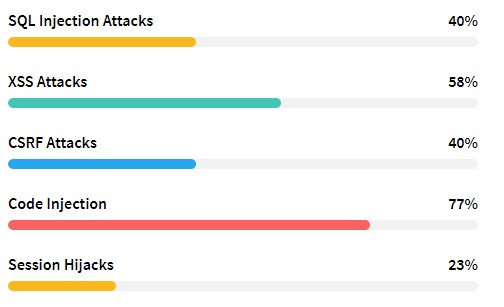
Figure: Web applications Attacks
To stay away from that, each organization needs to anchor their edge. Yet, since its critical part is currently involved by the organization's web applications, the protections against programmer assaults must be executed inside the real applications.Timely inspections of these defenses before and after an application release will help avoid critical situations.
